Applied Intelligence Lab
A research-driven lab that builds scalable intelligence systems, delivers expert services, and trains teams across threat intelligence, fraud operations, digital investigations, malware analysis, risk analytics, and cryptographic security.
Scalable Intelligence Platforms
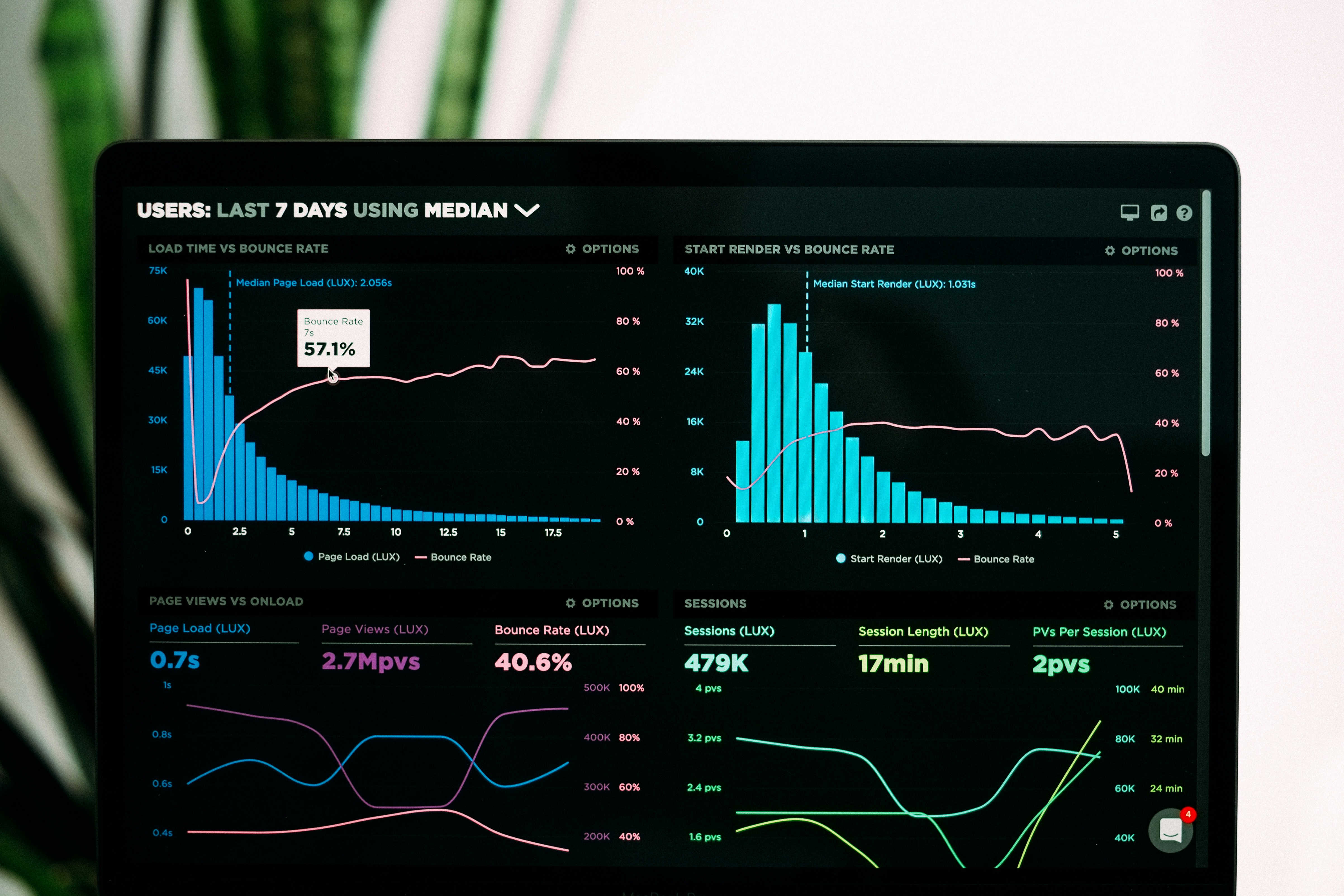
We design and ship production-grade systems that turn complex signals into operational intelligence — from ingestion and correlation to risk modeling, investigations, evidence, and executive reporting.
- ✔ Signal ingestion, enrichment & correlation engines
- ✔ Graph intelligence, scoring, anomaly & risk modeling
- ✔ Audit-ready outputs: timelines, reports, evidence packages